In technology I do so very much hate wastage. Wastage of the resources that go into manufacturing a product and wastage of time in dealing with low quality and unreliable products. Disruption to functioning networks and setups is also a real pain point in organizations and at home. Every device we upgrade whilst it (usually) has its pros the con is certainly the investment of time that goes into migrating your data and settings to it.
The endless upgrade-itis of technology.
Now don’t get me wrong, I like cool tech as much as the next sunlight averse geek but upgrading for incremental or sometimes useless features is scandalous in my opinion.
Take for example your average home router. Most folks take the one given by their broadband provider. It will tend to be a rebadged and restricted model. Often a variant of those sold by the likes of Netgear, Huawei and Thomson. It will have less features than the manufacturer’s own version and will be locked down to run on only your broadband supplier’s network.
On top of that every 1-2 years consumers are shipped a new device by their provider, with the old device relegated to a dusty closet at best or landfill at worst. The cost of the device is never ‘free’. It’s of course included in your monthly broadband bill.
This stack is not even exhaustive. There are at least four more routers from BT and various other broadband providers over the years which I couldn’t find for this photo shoot! Some of them were shipped to me despite telling my telco provider that I didn’t need one!
Some of us however try to improve the above state of affairs – those few of us who purchase aftermarket routers for their home networks. It’s a great shame that so few of us do so because the gains are not only less disruption to your home network as you’re forced to swap one router for the next, but the improved feature set, security and fuzzy warm goodness of an aftermarket device are significant.
Through the course of my life with tech I’ve been through many routers from many manufacturers. Seldom do I come across one where I think won’t need to buy another! A piece gear you know is so damn good you’ll never need upgrade again. At the risk of making a 640K level faux pax I declare that I have found a final statement when it comes to routers - pfSense.
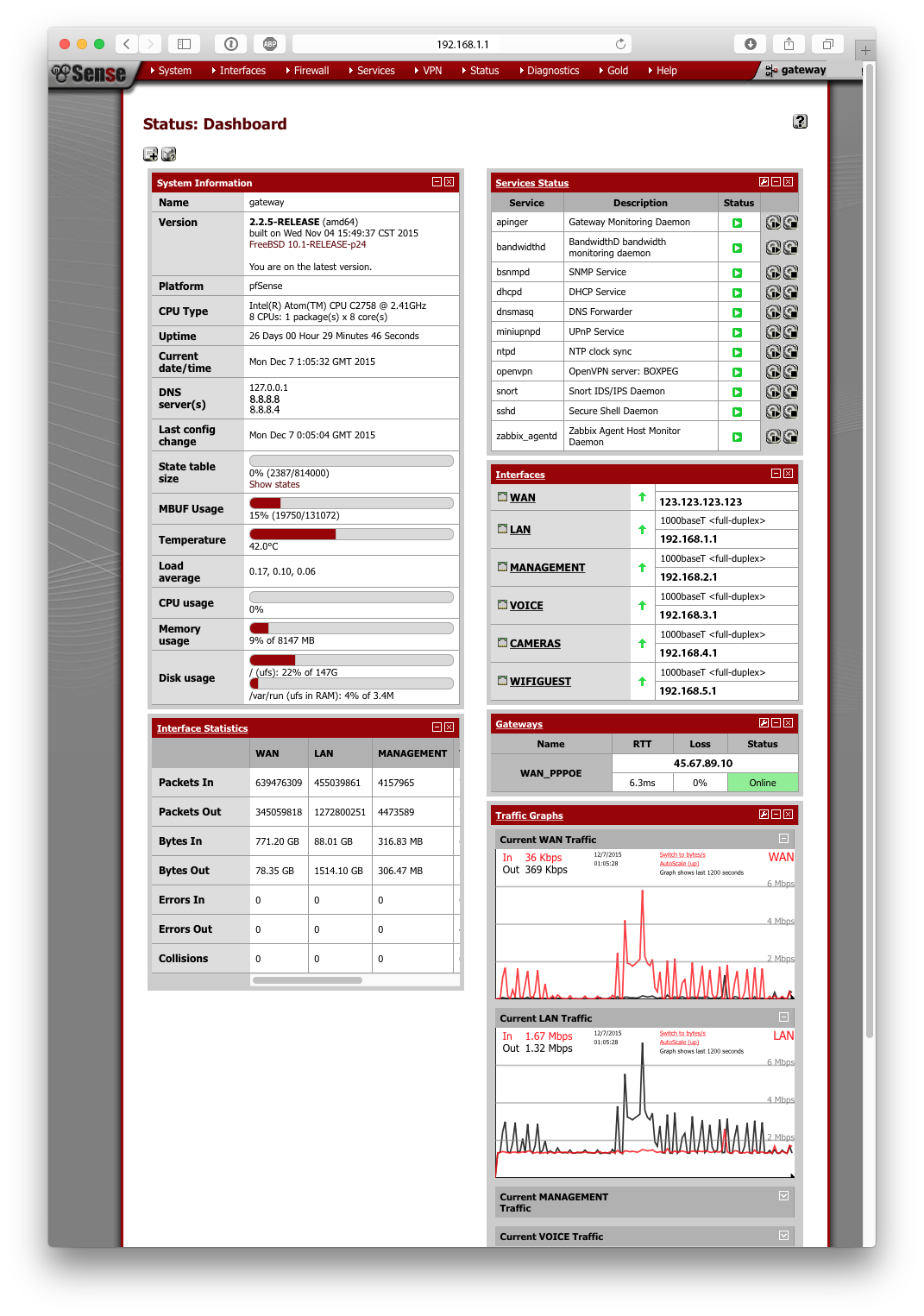
pfSense is without doubt the best router software I have ever used. It’s easy to use and sky’s the limit as far as what you’d like to do.
Want to block your teenager’s pesky Peer-to-Peer habits? No problem. Prioritize VoIP or web browsing? Consider it done. You can rate limit IPs on your local network, create whitelists, blacklists, have a local cache to save bandwidth so you don’t download the same file or image twice, you can even load balance across multiple WAN connections (which works damn near flawlessly) – the list of features just goes on and on.
There are all kinds of cool packages (86 at time of writing) which you can deploy with a single click. Packages like Snort which offers intrusion detection and prevention, monitors packets and looks for suspicious activity like incorrect HTTP headers, SSH and PDF exploits. Any sneaky traffic and Snort blocks the offending host for a defined period (or permanently), stopping any would be attackers in their tracks.
Proxy caching with the Squid package lets you cache images and downloaded files like updates for your iPhone, Android and Mac/Windows machines. No file needs to be downloaded more than once since Squid caches it and serves up the cached copy to subsequent clients – conserving your bandwidth if you’re on metered broadband as well as speeding up your internet browsing.
If you’ve ever wondered which machine’s hogging all your bandwidth wonder no more, there are at least three packages which let you monitor bandwidth and specifically bandwidth per client.
If you need a super-secure VPN you got it with L2TP/IPSec and OpenVPN offering client to server and server to server tunnels making it straightforward to setup connectivity between users and remote sites.
To cap it all off the basic core features are very comprehensive. There’s superb DNS functionality with DNS Caching and forwarding per domain with multiple DNS servers for fallback. There’s comprehensive VLAN support with per VLAN firewall rules, excellent DHCP support with per interface/VLAN DHCP services, DHCP reservations and DHCP options like NTP, TFTP and failover.
Everything is managed via a capable and stable Web GUI. No need for shell diving if you’re uncomfortable doing that and of course, lots and lots of monitoring options from SMART, to system temperatures, firewall traffic, DHCP status, VPN status and much, much more.
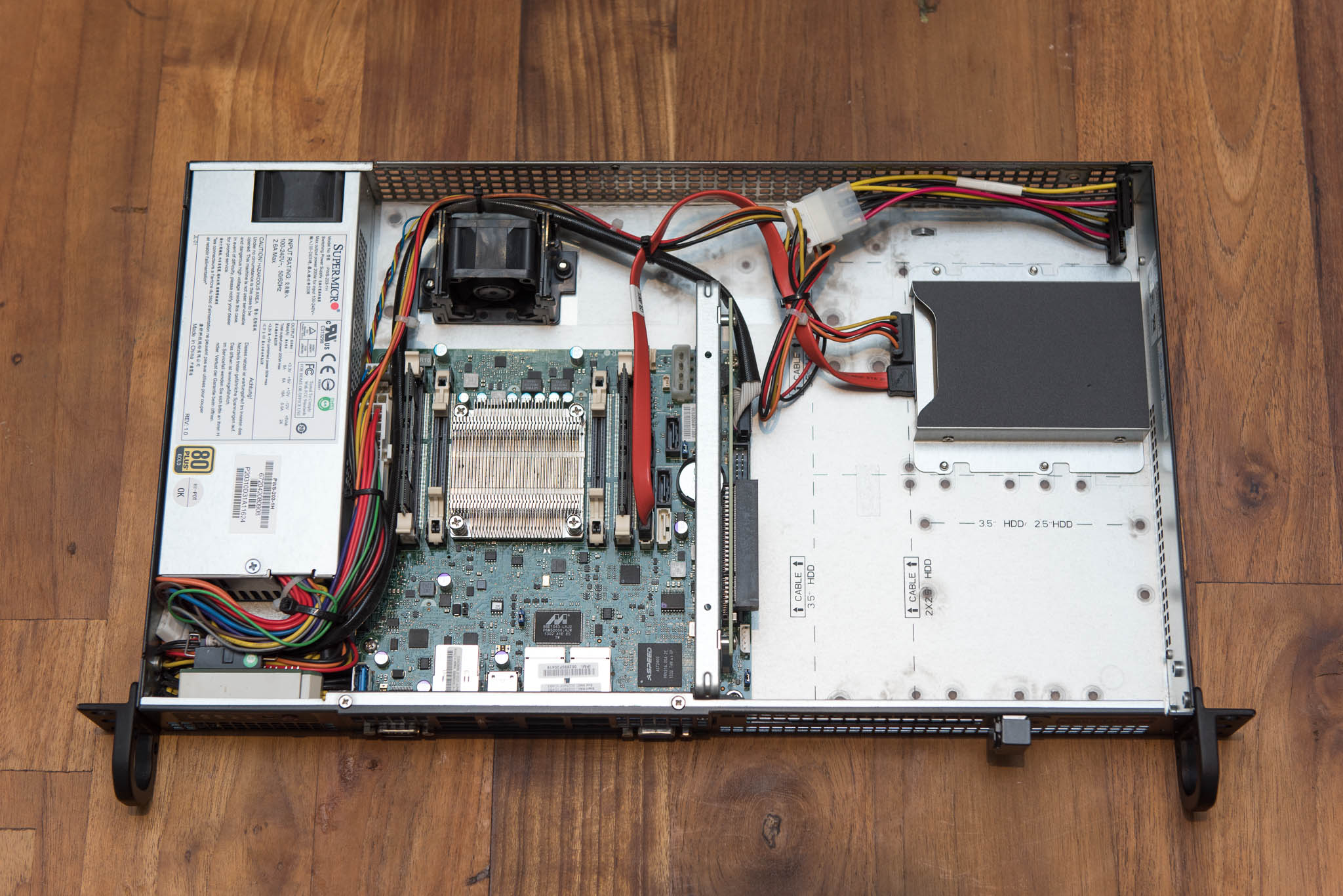
One great point about pfSense is that it’s a distribution. It runs on whatever hardware you have at hand. Or you can choose a compatible server to deploy it on. Keeping with the theme of final statements I chose the latter and picked up a Supermicro 5018A-FTN4.
Wow. This thing kills it. An eight core Intel Atom CPU, up to 64GB of RAM (ECC even!), space for 4x 2.5″ SSDs, IPMI and all in a form factor which consumes 20W at load and is pretty quiet as far as server kit goes (33 dbA).
It wasn’t cheap at $900 so if you don’t need this much power you can purchase an excellent two port, compact and fanless variant from pfSense direct for $300. I’d recommend the $50 SSD addon if you want to install packages like Squid, or Snort. The main difference between the various boxes is the amount of bandwidth each box can route, especially when using encrypted VPN connections. For home users the basic model should be more than enough to last you many, many years of solid use.
Supermicro 5018A-FTN4 Tweaks
If you’re using the Supermicro 5018A-FTN4 you might have to make the below modifications to get it to run. I originally deployed pfSense 2.1 and 2.2 is now out so the below might not all be necessary:
Preventing MBUF from maxing out
It seems the I354 chipset can cause kernel panics. Borrowing from JeGr’s tip add the following lines to /boot/loader.conf.local:
kern.ipc.nmbclusters="131072"
Enabling TRIM for SSD
Firstly use an Intel SSD. Not Samsung, not Crucial. Intel.
Login with SSH or locally and open a shell
- Run
/usr/local/sbin/ufslabels.sh - Add
ahci_load="YES"to/boot/loader.conf.local - Reboot
For some reason TRIM_set didn’t work for my pfSense gateway I had to:
- Start pfSense in single user mode.
- Run
/sbin/tunefs -t enable / - Reboot
Once the machine has rebooted check the status with: tunefs -p /
[2.1-RELEASE][admin@pfSense.hemma]/root(1): tunefs -p /
tunefs: POSIX.1e ACLs: (-a) disabled
tunefs: NFSv4 ACLs: (-N) disabled
tunefs: MAC multilabel: (-l) disabled
tunefs: soft updates: (-n) disabled
tunefs: gjournal: (-J) disabled
tunefs: trim: (-t) enabled
tunefs: maximum blocks per file in a cylinder group: (-e) 2048
tunefs: average file size: (-f) 16384
tunefs: average number of files in a directory: (-s) 64
tunefs: minimum percentage of free space: (-m) 8%
tunefs: optimization preference: (-o) time
tunefs: volume label: (-L)</code></pre>
Once done you should have a TRIM enabled pfSense install on some seriously kick ass hardware.